ADMINISTRATIVE INFORMATION
- Approval Authority: Vice Chancellor for Finance, Information Technology
- Responsible Administrator: Chief Information Officer (CIO)
- Responsible Office: The Office of Cybersecurity
- Policy Contact: Chief Information Security Officer (CISO)
- Approval Date: December 2021
- Effective Date: December 2021
- Last Revision Date: April 2023
POLICY STATEMENT
This policy establishes rules that govern the response to security incidents that impact Vanderbilt University’s information and technology systems.
REASON FOR POLICY
The Incident Response Policy (“IR Policy”) provides the structure and activities required to effectively respond to an information security incident and minimize negative impact to the confidentiality, integrity, and availability of institutional data and its information technology (IT) assets.
This IR Policy cannot anticipate and provide guidance for all potential information security incidents. Vanderbilt leadership and incident responders must consider the current situation, business impact, and security needs of the university and balance those against the guidance provided by the IR Policy.
The Office of Cybersecurity will review this policy annually with feedback collected from representatives across VU to understand new concerns and dynamic requirements to best serve the VU community and adhere to VU Information Security Principles listed in the Information Security Policy.
SCOPE
This policy applies to the entire Vanderbilt University community including, but not limited to, faculty, staff, students, contractors, post-doctoral fellows, temporary employees, and volunteers (collectively called “VU Community Members”). All IT assets used to collect, transmit, process, store, or host institutional data are in-scope for this policy.
POLICY
The Chief Information Security Officer (CISO) shall oversee and is responsible for institutional incident response strategy and activities.
A. INCIDENT REPORTING
A Security Event is an observable activity in a system or network that warns of potential harm to Vanderbilt University institutional data or IT Assets. Not all security events become security incidents.
VU Community Members must immediately report security events to the Office of Cybersecurity by phone at 615-343-9999 or submit a ticket online.
Examples of security events to report include, but are not limited to:
- Compromised user account;
- Compromised endpoint (e.g., malware, keylogger, ransomware, etc. detected on a user’s desktop, laptop, or other device);
- Compromised server (e.g., malware, unauthorized use/access, unusual activity);
- Compromised Vanderbilt-owned websites (e.g., website defacement);
- Compromised infrastructure (e.g., router, switch, firewall, ICS device); or
- Unauthorized exposure of sensitive data (especially high risk data types).
While awaiting triage by the Office of Cybersecurity, stop using the device in question immediately. Do not turn off the device as this could result in the loss of valuable forensic evidence. Do not attempt to investigate or remediate the issue as this could damage valuable forensic data.
B. INCIDENT RESPONSE PHASES
In contrast to a security event, a Security Incident is harm that has been realized or will be if not immediately addressed. If a security event is a fire alarm, a security incident is smoke or a fire.
The Office of Cybersecurity will work quickly to analyze detected alerts and reported events. Only Cybersecurity can confirm if an event is an actual incident. If confirmed, they will follow the VU Incident Response Plan (IR Plan).
The Office of Cybersecurity is responsible for establishing and maintaining an IR plan that outlines incident response strategy and steps. This plan will align with the most recent version of NIST Special Publication 800-61: Computer Security Incident Handling Guide.
Figure 1. NIST 800-61 Incident Response Lifecycle
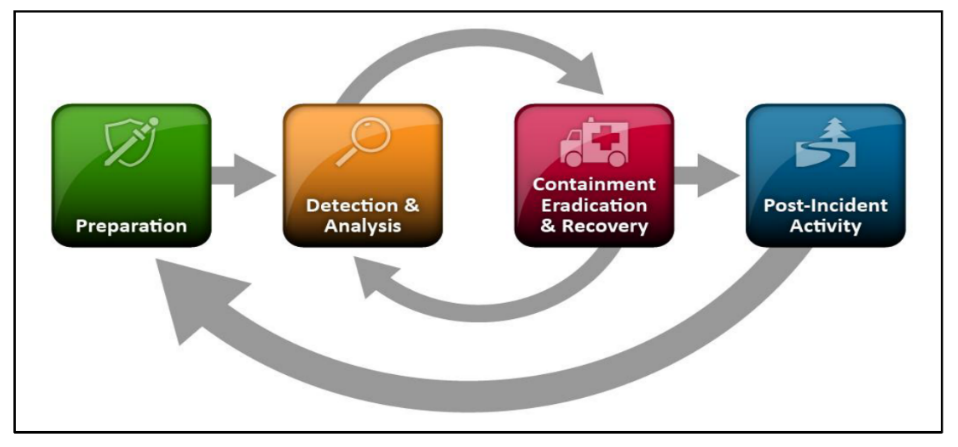
The IR Plan outlines:
- VU’s organizational approach to incident response;
- How VU determines, categorizes, prioritizes, and escalates security incidents. This outline aligns with the institutional Risk Classification Matrix; and
- VU’s communication and hand-off strategy with other campus offices and programs (e.g., Operational Continuity Management, Special Situations Team).
The IR Plan is an internal, confidential document that the VU Computer Incident Response Team (VU CSIRT) reviews regularly, no less than annually. Section D below, details the VU CSIRT purpose and membership. On at least an annual basis, the Office of Cybersecurity will coordinate a test exercise (i.e., a table top) to practice preparedness, exercise the IR Plan, and measure its effectiveness.
The VU IR Plan is a parent, institutional document. Should they exist, any school/department/unit level IR Plans that are specific for that area must align with VU IR plan and IR policy (e.g., area specific IR Plan for Controlled Unclassified Information, Payment Card Information IR Plan).
In response to an incident that poses an imminent threat to the university, the Office of Cybersecurity is authorized to take necessary steps to contain and/or disrupt malicious activity including, but not limited to, expediting changes to IT Assets, monitoring/retrieving relevant system records, and disconnecting systems from the network. At all times, the Office of Cybersecurity team will take careful consideration to minimize interruption to the operations of VU.
VU Community Members are required to fully cooperate in support of security incident investigations, consistent with the Appropriate Use of Technology Assets Policy. Cooperation may require actions such as resetting passwords and granting the Office of Cybersecurity access to a compromised device for forensic analysis.
The CISO, in coordination with the VU CSIRT and VUIT Senior Leadership, may involve external firms to facilitate incident response processes/phases.
C. INCIDENT COMMUNICATION
Information regarding security incidents is Level 2 Institutional Use Only, at a minimum, and incident knowledge is limited based on a need to know. The Office of Cybersecurity will communicate updates promptly to appropriate individuals and groups. The CISO shall communicate and escalate security incidents to appropriate governance bodies, campus offices and programs according to the IR Plan.
Where appropriate or necessary, the VU CSIRT, along with the Office of the General Counsel (OGC), will determine and coordinate reporting requirements to individuals and/or external entities, such as law enforcement or government agencies.
D. VU COMPUTER SECURITY INCIDENT RESPONSE TEAM (VU CSIRT)
The CISO is responsible for establishing and managing the VU CSIRT. Membership includes cross-campus representatives to provide a robust, effective, and cross-disciplinary business response to a security incident. The VU CSIRT coordinates communications to affected individuals and/or external entities. Both core and consultant members may be brought in as needed. Core membership includes the following:
- Chief Information Security Officer (CISO)
- Chief Information Officer (CIO)
- Risk and Insurance representative
- Finance representative
- Communications representative
- Enterprise Risk Management representative
- Disaster Recovery representative
- General Counsel representative
- Public Safety representative
E. IR RESPONSIBILITY SUMMARY
Incident response activity | Responsibility |
Report security events to VUIT | All members of the VU community |
Cooperate during security investigations | All members of the VU community |
Establish, maintain, and test the VU IR Plan | Office of Cybersecurity |
Detect and analyze security events | Office of Cybersecurity |
Confirm security incidents, determine classification, and contain/eradicate security threats | CISO and Office of Cybersecurity |
Escalate security incidents | CISO |
Determine and manage reporting requirements (internal and external) | VU CSIRT and OGC |
Develop and communicate lessons learned | CISO and Office of Cybersecurity |
Activate cyber liability insurance | Risk and Insurance Management |
EXCEPTIONS
On a rare occasion, a security policy exception may be considered depending on the impact to the university mission and security risk(s) introduced. Exception requests must be submitted to the VU Chief Information Security Officer for evaluation and risk assessment. The CISO, or a delegate, will grant or deny the request based on the level of risk.
ENFORCEMENT
Any VU community member that violates this policy may be subject to disciplinary action up to and including termination. The Chief Information Security Officer will refer violations to university units (e.g., Student Accountability Office, Human Resources, and Deans) as appropriate. Violations may also constitute a violation of state or federal law and individuals shall be accountable as applicable.
DEFINITIONS
PROCEDURES
To report a security event or incident, call 615-343-9999 or submit a ticket.
FREQUENTLY ASKED QUESTIONS
RELATED DOCUMENTS/POLICIES
HISTORY
| Review Date | Summary of Changes |
| April 2023 | Added section for guest network access, updated boilerplate language |